The traditional calendar mark indicating Summer’s watch over the planet is coming to an end is just around the corner. Some cities will experience high temperatures for a few more months while others will start donning light jackets and anticipate the changing of arboreal colors.
The age group that experiences the most drastic change during this time of year are the high school graduates. Some will start a job or an apprenticeship, others will be off to college. All will be part of a right of passage that will see bittersweet tears at the end of August as most friends scatter in different directions. Everything that was known up until this point is about to change.
The summer after high school graduation is a magic time. Teenagers have the freedom that comes from a loosening parental grip as they are ushered closer toward the border of adulthood. But, below them, the safety net that caught their falls during high school will inevitably be put to the test one more time during the last summer of their youth. It’s a good thing. The kids need to make sure the net still works, even though they’ll deny that they do, and parents will want to carry the weight of the drama one more time before it relocates to become a visitor instead of a tenant of the family home.
It’s been a great summer. And for those who graduated high school last spring, it has been the only summer of its kind.
There we were, a virtual mosaic sampling of the states that make up this great United States of America: One Tennessean, a Texan, an Arizonan and me, a native Pennsylvanian. Realizing that Labor Day and the end of summer was fast approaching; we crammed ourselves into an SUV, along with all of our camping gear, and headed off, out of state, for a late summer weekend.
Midway to our destination the telltale sound of an aluminum can opening called our attention to the backseat.
Our born and bred Texan brother had opened himself a can of beer. Screeching brakes was the next sound that was heard by all.
“Are you freakin crazy, you can’t drink a beer in the car,” we all screamed at him simultaneously.
He looked at us dumfounded, “You can in Texas,” he said shrugging his shoulders. Withering under our collective glare he added, with considerable less authority, “as long as you aren’t driving?”
While we all waited by the side of that lonely highway, he disposed of the rest of his beverage.
“You know,” he said bitterly in between sips. “Prohibition is over.”
Yes it is, and well, no it isn’t.
National Prohibition, also called the “Great Experiment” was brought into being by the 18th Amendment to the Constitution in 1919, the so-called Volstead Act which in combination with other laws, prohibited “…the manufacture, sale, or transportation” of “intoxicating liquors” in the United States.
As a result crime soared, tax revenue was lost and the United States limped along into what would become the Great Depression. Franklin Roosevelt won the 1932 Presidential election based in large part on his promise to repeal the 18th Amendment. He did so incrementally, beginning by legalizing the sale of beer, and ending with the 21st Amendment to the Constitution (ratified in 1933) which effectively repealed the 18th, the first and only time an amendment to the Constitution has ever been repealed.
The second part of the 21st Amendment reads:” The transportation or importation into any State, Territory or possession of the United States for delivery or use therein of intoxicating liquors, in violation of the laws thereof, is hereby prohibited.” Language that effectively means that while National Prohibition might be repealed, state prohibition is left up to the States themselves.
As a result the laws governing liquor vary greatly from state to state. Sometimes even town to town within a state. Here are some particular oddities in with which you may or may not be familiar.
- About 8 percent of this nation of ours is currently “dry”, an area encompassing about 20 million people.
- Moore County, Tennessee is a dry county, which is odd because it is also the site of the Jack Daniel’s whiskey distillery (a nationally recognized historical place). Tourists may buy souvenir bottles, but if they drink them on the porch-like the advertisements-they will be breaking the law.
- Almost half of Mississippi is “dry” prohibiting the production, advertising, sale, distribution, or transportation of alcohol completely. Many of those counties have been dry since 1907, which is over twenty years before National Prohibition began.
- Kentucky (the home of Bourbon whiskey) lists 55 of its 120 counties as completely “dry”, including many that made up the original Bourbon County (although not the much smaller county that now bears that name).
- In Pennsylvania (the birthplace of rye whiskey) the only entity allowed to wholesale alcohol is the state, making the Pennsylvania Liquor Board one of the largest single purchasers of alcoholic beverages in the world.
- Arizona goes another route, actually prohibiting any county or town from prohibiting alcohol.
If all of this sounds confusing, that is because it is. Which is why if you are heading out of state on a late summer weekend-and plan to imbibe-you just might want to be sure what the local laws are.
Once my friends and I had sorted out the regional legalities of our little camping trip I had time to reflect on a couple of things;
- Drinking and driving never, ever, mix.
- Texas changed their open container law on Labor Day 2001, banning all open alcoholic beverages in all motor vehicles, coerced by the withholding of federal highway funds.
- The Feds also used that same withholding of highway funds to encourage state governments to mandate a national 21 year old drinking age. (Maybe old dogs can indeed learn new tricks).
- It might just be time for me to find some new friends.
I’m walking with Nico through the hallways of the convention area of the Riviera Hotel in Las Vegas. There is a distinct old school feeling at the Riviera that reminds one of the days when Las Vegas was run by the family. Walking swiftly Nico tells me that we might see security expert Chris Paget get arrested during his presentation.
“Arrested?”
As we get closer to the hall where Paget is presenting, I can hear someone yelling, “if you have a GSM cell phone, your call may be intercepted. If you do not want this to happen, then turn off your cell phone.” The vociferous warning is supported by the flyers I see haphazardly taped to the walls.

photo by Lou Lesko
Using a laptop, a transmitter broadcasting over a ham-radio frequency and two antennas, Paget has created a GSM base station which all the mobile phones in the near vicinity have been duped into thinking is a legitimate AT&T cell tower. “When the phone is looking for a signal, it looks for the strongest tower. This [his setup] offers the best signal,” he explains. On the laptop screen he shows a list of phones, mine included, that are connected to his fake network. The threat of arrest comes from the FCC. Should Paget intercept a voice or data transmission from one of the phones connected to his $1500 dollars worth of equipment and open-source software, he will be in violation of the law. I honestly can’t decide if I want to see that happen or not. The sensationalistic side of me would love to see the drama, but the rational side of me is taken with Paget’s enthusiasm and blazing intelligence. More importantly, he has revealed an inherent security weakness with 2G technology. A weakness that can be fixed by moving mobile networks to 3G or encrypting 2G connections.
This is an example of what happens every year at the DefCon hacker conference in Las Vegas. Passionate hackers present their knowledge and capabilities, often times skirting the very fringes of legality. However, if you think that this is a convention for geek criminals, then you’ve been watching too much NBC.
Have you ever locked yourself out of your home and had to try to break in? There is sense of accomplishment in succeeding. Then there’s the slightly disturbing revelation that if you can break into your place as an amateur, a professional could do five times faster - so you look at your exploit and fix the breach. DefCon is like that.
The activities and experiments that take place at DefCon, along with the information reported here has an enormous impact on our daily lives. These are the people that look with significant scrutiny at all manner of security systems that are found everywhere from the internet, to mobile communications to household door locks. And then they try to hack them. After attending three years in a row I can tell you that very few people here hack with a nefarious intent, but rather they do it for the challenge, and the thrill that comes from circumvention. From these efforts shortcomings are revealed and changes are made by the targeted industry to plug the security holes.
A poignant example of this is when I attend a presentation on electronic door locks. The presenters reveal significant weaknesses in several brands of electro-mechanical locks. When I say weaknesses, I’m talking about things like a household version of a bio-lock that uses a fingerprint scan for entry being defeated, easily, by a paper clip. The presenters alerted all the manufacturers of all the locks they hacked to allow them the opportunity to fix the problems. Not all responded. Ironically one of the most secure locks they demonstrated was a 4000 year old Egyptian tumbler lock.
DefCon is a vast mix of cultures as well as being a culture unto itself. The DefCon staff who are responsible for security and general order are called “goons”. The DefCon badges are electronic, hackable and showcase an anti-establishment, almost cyber punk aesthetic. If designer Alexander McQueen were still alive, he would find much inspiration here.
Walking around the halls are people in dark clothes, ripped jeans and mohawks talking to people in golf shirts and khakis. Its is a welcome antidote from the Hollywood environ where I live. Social status here is based on knowledge and accomplishment and not on clothing labels or car marques.
That is not to say you shouldn’t watch your back here. There are unwritten rules like; don’t ask anyone where they work, and don’t use any ATMs within a two block radius of the Riviera hotel. There are government agents here, as well as white collar criminals. If you are press, you are asked to be obvious in displaying your credential, and to ask permission before shooting pictures of anyone. A rule that NBC Date Line undercover reporter Michelle Madigan ignored in a legendary incident at DefCon 15 in 2007 where she was publicly outed and escorted from the conference. Madigan refused four different offers from DefCon for legitimate press credentials and then proceeded to register as a regular attendee. She brought a pinhole camera into the conference to allegedly portray DefCon in a sensationalistic, scaremongering way to shock the people in the midwest. There were a number factors that led to her discovery, but the most egregious from a DefCon perspective was panning her pinhole camera across the Capture the Flag room, a room where it is absolutely forbidden to have any sort of visual recording device. DefCon has a responsibility to protect the identities and methods of the people in the Capture the Flag competition so they can attract the brightest hackers to compete.
Capture the Flag pits elite hackers against elite hackers in a cyber game of network attack and defense that goes on 24 hours a day. CTF takes place in a large hotel conference hall. The hall is lit by down lights, huge video projections on all of the walls, and clouds of monitor glow which emanate from groups of tables that are spaced about twenty feet from each other. Each group of tables is a CTF team. Up on the walls are projected videos ranging from movie snippets to material from YouTube. Also projected is each team’s status in the contest. In the center of the room is an elevated command and control platform overseeing the contest and providing the visuals.
Pizza boxes and various caffeinated beverages are strewn between rows of laptops in each team section. The room is mesmerizing. I was given limited and supervised photographic access to the room, provided I asked everyone who had the potential to be in my frame their permission before clicking the shutter. Also I was strictly forbidden from revealing any of the details on the computer screens.

Capture the Flag - photo by Lou Lesko

The Korean Capture the Flag Team - photo by Lou Lesko
Elsewhere at DefCon there are hacking villages; small rooms with lots of hands on demonstration tables and brilliant people manning them where you can learn a myriad of things from how to pick locks, to electronically hacking the firmware of your hackable DefCon badge.
Along with the DefCon badges, which everyone who attends receives, a limited number of Ninja badges were handed out by Ninja Networks, a hacker group based in the Pacific Northwest. The badges are part video game and part electronic invitation to the exclusive Ninja Networks party. These extraordinary pieces of innovation, that were underwritten by Lookout Mobile Security, are the product of Amanda Wozniak, who created the hardware, and Brandon Creighton who wrote the firmware. The character on the screen of the Ninja badge starts to battle other Ninja characters of other badges when the badges are in proximity to each other. In order to get to the top level of the badge there are different tasks that have to be accomplished that include an electronic scavenger hunt, cryptographic puzzle solving and a donation to the Electronic Frontier Foundation, a non-profit organization devoted to protecting digital rights.
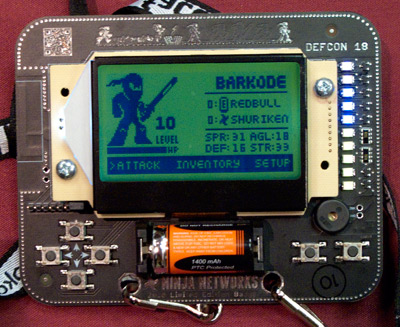
Ninja Badge belonging to Barkode - photo by Lou Lesko
I caught up with Miss Wozniak at the Ninja party. “Passionate” is inadequate in describing the alacrity she assigns to her craft. As I interviewed her she excitedly took apart my badge and showed me how it worked. She also pointed out that the electronic piece was completely modular and ready to be repurposed for experimentation or a new creation. It is inspired forward thinking and functionality.
Back at the conference I’m walking through the halls where there is seemingly no end to cool hacking events. A contest entitled Gringo Warrior is described as:
Participants in Gringo Warrior will have five minutes to free themselves from handcuffs, escape from their “cell”, get past a guard, retrieve their passport from a locked filing cabinet, leave through another locked door, and make their escape to freedom. The course will offer a variety of locks representing a range of difficulty, allowing participation by people of all skill levels. Points will be awarded based on the time of completion as well as the difficulty of locks attempted. The best warrior of all wins the grand prize!
It’s a series of locks that the contestant has to pick starting with hand cuffs at one end of the stage, and ending with a door lock on a stand at the other.
Not far away is an impromptu salon dishing out only one kind of hairdo. A mohawk. For a fifteen dollar donation that goes to the Electronic Frontier Foundation, you can walk a way with a new look, or as is the case that I’m seeing over and over, a cleaned up version of your original hawk. There is a rumor circulating that the Guinness Book awarded the tallest mohawk to a DefCon attendee this week. The disclaimer stating that the people performing the hair artistry are not professionals doesn’t seem to intimidate anyone. Every time I walk past the salon, business is brisk.

Mohawks for EFF - photo by Lou Lesko
If you’re one who dismisses the DefCon attendees as group of misfits and social pariahs then you probably have the same password for ninety percent of your online existence. Which means you are doomed. Because as clever as you think you’re being by using your dog’s birthday backwards as a secure key, you’re no match for the people that I’ve met. There is no more greater ignorance online than that of an average internet user who believes what the mainstream media says about hackers and internet security. There is much more going on in this constantly changing and evolving technological world than those predictable stereotypes.
The attendees at DefCon are pioneers on a myriad of levels. Socially they challenge convention on every strata. Fashion-wise there are no boundaries and norms, just personal styles that clothe intelligent minds. In the realm of the internet, communications and other security genres, there is no equal.

photo by Lou Lesko
You may argue that these hackers have a proclivity to criminal behavior which is why they do what they do. I’ll tell you are wrong. Yes there are criminal intentions to be found at DefCon, but so are there to be found in your office. Every niche of society has a dark element. But that’s not the majority of what you see in society, or here at DefCon. The sense of community and public education is overwhelming, as is the need to share, albeit anonymously, successful hacks that reveal weaknesses in the various security infrastructures that affect all of our lives.
Recently in the news there have been a number of stories telling of various governments, including our own, that are lobbying to try and get more access to the data of our personal online habits. This is an unconscionable thought to me and to probably many of you reading this. Sadly we have very few tools to protest such agendas should they be advanced. But I know a group of people who are passionate about online freedom and have the means to make a stand against insurgencies into your private online life. Many of them can be found at DefCon.
Photographer Steve Winter has an unusual experience when he enters an Apple store. The elusive snow leopard, which he chased for 10 grueling months in northern India, is now everywhere; one of his images is being used by Apple’s newest felinely titled operating system:
The image being used by Apple shows a snow leopard, captured by one of Steve Winter’s camera traps, skulking high in India’s northern mountains.
National Geographic estimates that as few as 3,500 snow leopards exist in the wild. Some have been spotted at altitudes as high as 18,000 feet. Not surprisingly, few have been successfully captured on camera. Less surprisingly, Geographic wanted to change that.
Read and hear the rest on NPR here.
The right and the left in America don’t agree on much, but for decades, they’ve shared one basic belief: You can’t trust the mainstream media. On the left, it was the New York Times and the big TV networks beating the drums about weapons of mass destruction and leading us in to the Iraq War. Or it was the corporate control of the major media, and the consolidation of ownership. Or it was Rupert Murdoch.
On the right, it was, of course, the famous “liberal media.” And for those who came of age with the blogosphere, it was the hated “gatekeepers”, those elite, arrogant editors who controlled what made it onto the front pages – and more important, what didn’t.
I’m one of those critics, too. As the executive editor of an alternative newspaper, I spend a lot of time talking about how the daily papers and the TV stations do a lousy job covering local news. I deplore the inaccuracy and bias of my local daily; I denounce the fluffy and superficial news broadcasts that ignore the real issues. I tease my town’s gatekeepers mercilessly; you think that crap is news? Why won’t you cover the real stories?
But a funny thing is happening in 2010: As corporate control of the news slackens, and the gatekeepers become less relevant, and media becomes so hyper-democratized that any fool with a $300 computer can become a publisher, some of us are starting to miss the old days.
You see, the media world has become so wide open that Americans are choking on information – and so much of it is either so utterly biased or factually inaccurate that nobody really knows who or what to believe any more.
The Shirley Sherrod affair made that point with such stunning clarity that it surprised political observers across the spectrum. Sherrod, a midlevel Department of Agriculture employee, became the latest victim of Andrew Breitbart, the blogger and online publisher whose fabricated and altered videos shattered an entire national organization.
In this case, Breitbart posted a heavily edited video of a speech Sherrod made to the NAACP. The excerpts made Sherrod look a racist who didn’t like white people — which corresponded precisely with the political narrative Breitbart was pushing.
Of course, sleazy political activists have tried to accuse their foes of all sorts of things over the years; the most insane, inaccurate stuff doesn’t typically stick. But this time around, a combination of new media technology, a split-second 24-hour news cycle and the willingness of agenda-driven talk radio to pick up on the smelliest scraps of gossip created a perfect political typhoon. Sherrod was fired, the Obama administration looked awful — and Breitbart, completely unrepentant, basked in the glory of celebrity and his soaring page views.
The sordid episode led Van Jones — a certified liberal activist and a member of the progressive political movement that has consistently blasted the mainstream media — to make an extraordinary confession: He misses Walter Cronkite. In a New York Times oped piece July 25th, Jones wrote:
“Anyone with a laptop and a flip camera can engineer a fake info-virus and inject it into the body politic. Those with cable TV shows and axes to grind can concoct their own realities. The high standards and wise judgments of people like Walter Cronkite once acted as our national immune system, zapping scandal-mongers and quashing wild rumors. As a step toward further democratizing America, we shrunk those old gatekeepers — and ended up weakening democracy’s defenses.”
This can’t go on forever. In a country as large and diverse as the United States, democracy can’t survive without honest reporters providing honest information that has some degree of credibility. At some point, the electronic media world will shake out — the Breitbarts of the world will become the equivalent of the Weekly World News, jabbering about space aliens and Elvis Presley’s clone. The more responsible outlets — the ones that have standards and principles — will become the accepted sources of reliable news that Cronkite and CBS once were.
The good news is that there will be more of them, and they’ll offer a broader spectrum of debate. The bad news is that we’re going to face a rough interregnum — a period when the old media have lost their credibility and are on the brink of collapse, and there’s so much new information slamming into our minds unfiltered and unedited that nobody knows if we can believe anything anyone says anymore.
And for anyone who really wants to make American politics work, that’s not a pleasant thought.
Tim Redmond is executive editor of the San Francisco Bay Guardian. He has won more than 30 journalism awards, including the Investigative Reporters and Editors Award for Outstanding Investigative Reporting and the Sigma Delta Chi Award for Editorial Writing. He is the First Amendment chair of the Association of Alternative Newsweeklies.












